If you are looking for How to Ensure Data Security in Cloud Computing - IndustryWired you've visit to the right web. We have 9 Images about How to Ensure Data Security in Cloud Computing - IndustryWired like How Secure is Your Cloud Data? - Barricade IT Security, Why Invest in Data Security in Cloud Computing | IT Briefcase and also How to Ensure Data Security in the Cloud Architecture | Bleuwire. Here you go:
How To Ensure Data Security In Cloud Computing - IndustryWired
 industrywired.com
industrywired.com computing industrywired
How Secure Is Your Cloud Data? - Barricade IT Security
 barricadeitsecurity.com
barricadeitsecurity.com Data Security In Cloud| Trends In Cloud Security | Cloud Computing
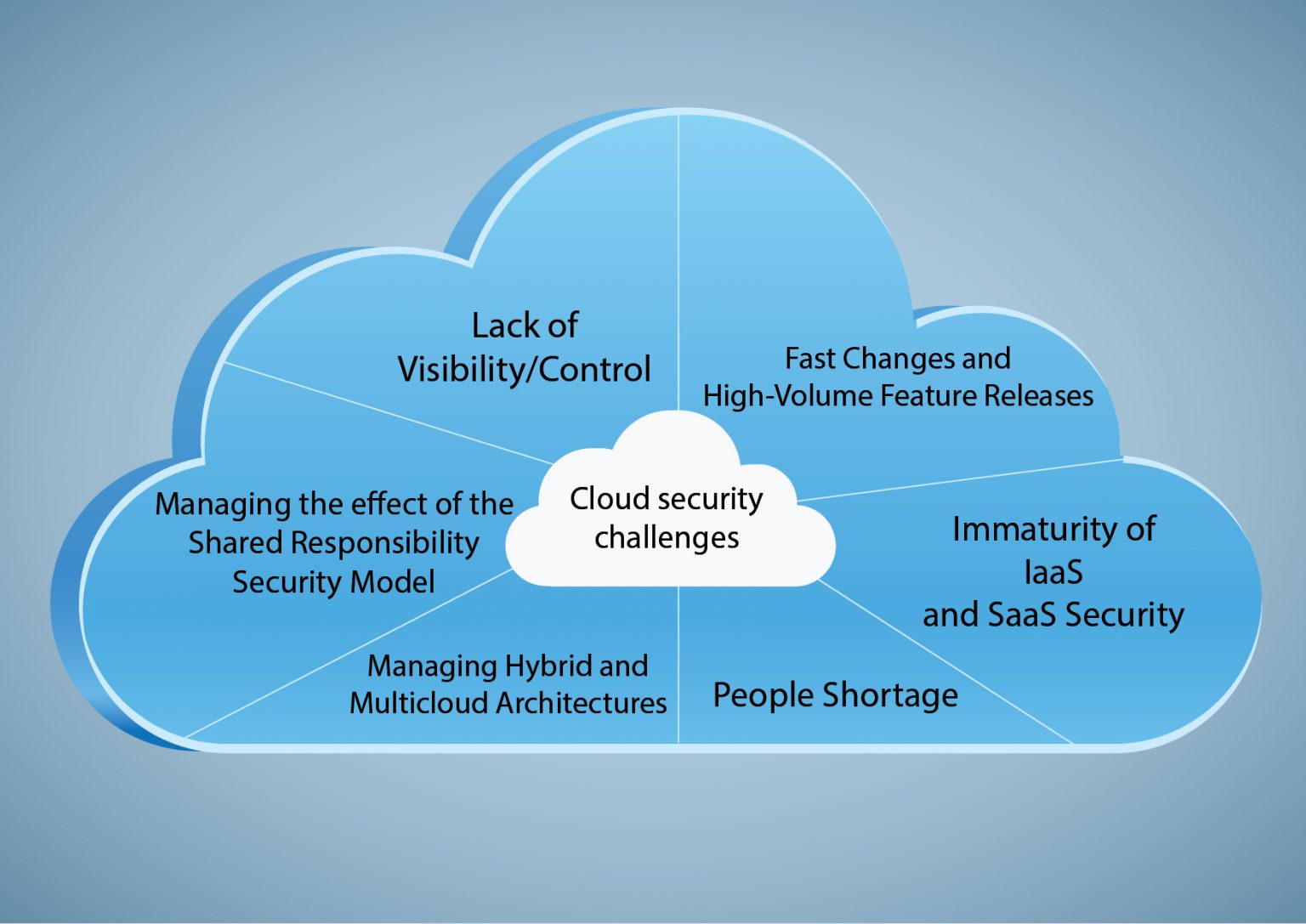 www.suntechnologies.com
www.suntechnologies.com visibility suntechnologies
Data Security Statistics - Understanding Cloud Data Security Risks
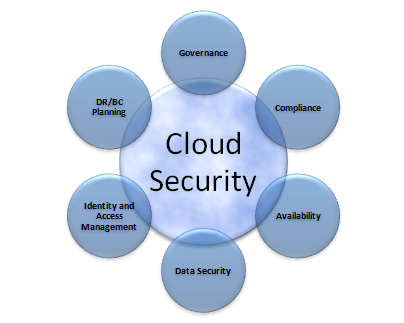 www.access-smart.com
www.access-smart.com security cloud computing data challenges issues risks related threats infrastructure clouds statistics key services safe sound why secure oep perez
Should You Trust Bill Gates With Your Cloud Data? – ShoeMoney
 www.shoemoney.com
www.shoemoney.com data cloud transfer cyber silent insurers insurancejournal tablet gates bill hurricane fear worst shoemoney security
How To Ensure Data Security In The Cloud Architecture | Bleuwire
 bleuwire.com
bleuwire.com cloud data security architecture ensure
Cloud Security: How Secure Is Cloud Data? - The .ISO Zone
 theisozone.com
theisozone.com duwen knoop virtuele impressão threats nuvola bottone virtuale spinge requirement encryption computing disa evolvement fedscoop importância qual entenda nube techrepublic
Why Invest In Data Security In Cloud Computing | IT Briefcase
cloud security computing data technology why business investment inquire owners starting days
A Cloud Built On Integrated Security - Intelligent CIO Africa
 www.intelligentcio.com
www.intelligentcio.com tco ivision
How secure is your cloud data?. Why invest in data security in cloud computing. Duwen knoop virtuele impressão threats nuvola bottone virtuale spinge requirement encryption computing disa evolvement fedscoop importância qual entenda nube techrepublic
if you are looking "id":33,"keyword_id":1,"name":"Cloud Data Security","scraped_at":"2022-12-16 03:31:17","created_at":"2022-12-16T03:31:17.000000Z","updated_at":"2022-12-16T03:31:17.000000Z","images":["id":253,"keyword_id":33,"url":"https:\/\/barricadeitsecurity.com\/wp-content\/uploads\/2019\/11\/Secure-Your-Cloud-Data-scaled.jpg","link":"https:\/\/barricadeitsecurity.com\/how-secure-is-your-cloud-data\/","title":"How Secure is Your Cloud Data? - Barricade IT Security","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.hFF9lP4142LtPx_3WC0hCQHaE8&pid=15.1","size":"2560 x 1707 \u00b7 jpeg","desc":"","filetype":"jpg","width":2560,"height":1707,"domain":"barricadeitsecurity.com","created_at":null,"updated_at":null,"id":254,"keyword_id":33,"url":"http:\/\/www.itbriefcase.net\/wp-content\/uploads\/2018\/04\/cloud-security.jpg","link":"http:\/\/www.itbriefcase.net\/why-data-security-in-cloud-computing-is-a-good-investment","title":"Why Invest in Data Security in Cloud Computing , Cloud Computing","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.XXF_rmBgqEzsWtGr6kUrGAHaFP&pid=15.1","size":"1536 x 1087 \u00b7 jpeg","desc":"visibility suntechnologies","filetype":"jpg","width":1536,"height":1087,"domain":"www.suntechnologies.com","created_at":null,"updated_at":null,"id":256,"keyword_id":33,"url":"https:\/\/www.intelligentcio.com\/africa\/wp-content\/uploads\/sites\/5\/2019\/12\/Cloud-security-1000-pic-scaled.jpg","link":"https:\/\/www.intelligentcio.com\/africa\/2019\/12\/19\/a-cloud-built-on-integrated-security\/","title":"A cloud built on integrated security - Intelligent CIO Africa","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.NtnGt2vHTdbaUzq5CqUHyQHaE8&pid=15.1","size":"2560 x 1707 \u00b7 jpeg","desc":"tco ivision","filetype":"jpg","width":2560,"height":1707,"domain":"www.intelligentcio.com","created_at":null,"updated_at":null,"id":257,"keyword_id":33,"url":"https:\/\/www.access-smart.com\/wp-content\/uploads\/2011\/12\/cloudsecurity.png","link":"https:\/\/www.access-smart.com\/data-security\/cloud\/","title":"Data Security Statistics - Understanding cloud data security risks","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.0WUjjUKDylyvpTqiNi7y0wAAAA&pid=15.1","size":"404 x 323 \u00b7 png","desc":"security cloud computing data challenges issues risks related threats infrastructure clouds statistics key services safe sound why secure oep perez","filetype":"png","width":404,"height":323,"domain":"www.access-smart.com","created_at":null,"updated_at":null,"id":258,"keyword_id":33,"url":"https:\/\/industrywired.b-cdn.net\/wp-content\/uploads\/2020\/01\/How_to-Ensure-Data-Security-in-Cloud-Computing.jpg","link":"https:\/\/industrywired.com\/how-to-ensure-data-security-in-cloud-computing\/","title":"How to Ensure Data Security in Cloud Computing - IndustryWired","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.hvKfFgzdEWYXyKPfBuTZUgHaEL&pid=15.1","size":"1200 x 677 \u00b7 jpeg","desc":"computing industrywired","filetype":"jpg","width":1200,"height":677,"domain":"industrywired.com","created_at":null,"updated_at":null, Bleuwire","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.FPaUVOfYDc14OduOLqsgjAHaE8&pid=15.1","size":"853 x 569 \u00b7 jpeg","desc":"cloud data security architecture ensure","filetype":"jpg","width":853,"height":569,"domain":"bleuwire.com","created_at":null,"updated_at":null,"id":260,"keyword_id":33,"url":"https:\/\/theisozone.com\/wp-content\/uploads\/2020\/08\/Cloud-security-risks-1536x939.jpg","link":"https:\/\/theisozone.com\/secure-cloud-data\/","title":"Cloud Security: How Secure Is Cloud Data? - The .ISO zone","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.wWoKosgNAZVgNZmERdQ5qgHaEh&pid=15.1","size":"1536 x 939 \u00b7 jpeg","desc":"duwen knoop virtuele impress\u00e3o threats nuvola bottone virtuale spinge requirement encryption computing disa evolvement fedscoop import\u00e2ncia qual entenda nube techrepublic","filetype":"jpg","width":1536,"height":939,"domain":"theisozone.com","created_at":null,"updated_at":null,"id":261,"keyword_id":33,"url":"https:\/\/www.shoemoney.com\/wp-content\/uploads\/2017\/07\/Cloud-data-security.jpg","link":"https:\/\/www.shoemoney.com\/2017\/07\/31\/trust-bill-gates-cloud-data\/","title":"Should You Trust Bill Gates With Your Cloud Data? \u2013 ShoeMoney","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.az5a7jG-95zOg_43VR9pkQHaE7&pid=15.1","size":"1688 x 1125 \u00b7 jpeg","desc":"data cloud transfer cyber silent insurers insurancejournal tablet gates bill hurricane fear worst shoemoney security","filetype":"jpg","width":1688,"height":1125,"domain":"www.shoemoney.com","created_at":null,"updated_at":null] this site you are coming to the right page. Contains many images about Cloud Data Security Data security in cloud| trends in cloud security. Don't forget to bookmark this page for future reference or share to facebook / twitter if you like this page.
No comments:
Post a Comment