If you are looking for 8 security benefits of cloud computing | Cloud infrastructure, Benefits you've came to the right page. We have 9 Images about 8 security benefits of cloud computing | Cloud infrastructure, Benefits like Five Best Practices for Cloud Security - United States Cybersecurity, Top 5 Best Practices for Cloud Security - Infosecurity Magazine and also Best Practices for Cloud Security. Here it is:
8 Security Benefits Of Cloud Computing | Cloud Infrastructure, Benefits
 www.pinterest.com
www.pinterest.com Implementation Of Cloud Security - H-X Technologies
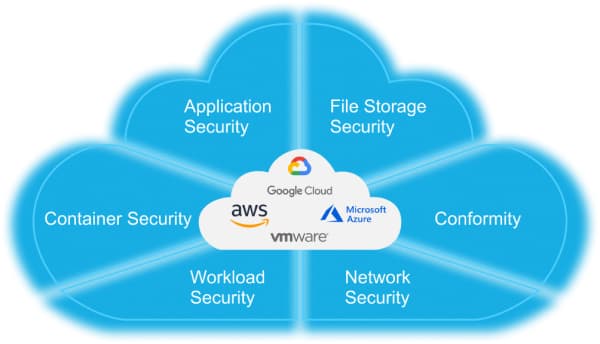 www.h-x.technology
www.h-x.technology Best Practices For Cloud Security
 www.slideshare.net
www.slideshare.net How Are Cloud Computing And Data Centers Related? | Connectria
 www.connectria.com
www.connectria.com cloud computing data centers related
Secure Your Data On The Cloud - Paperblog
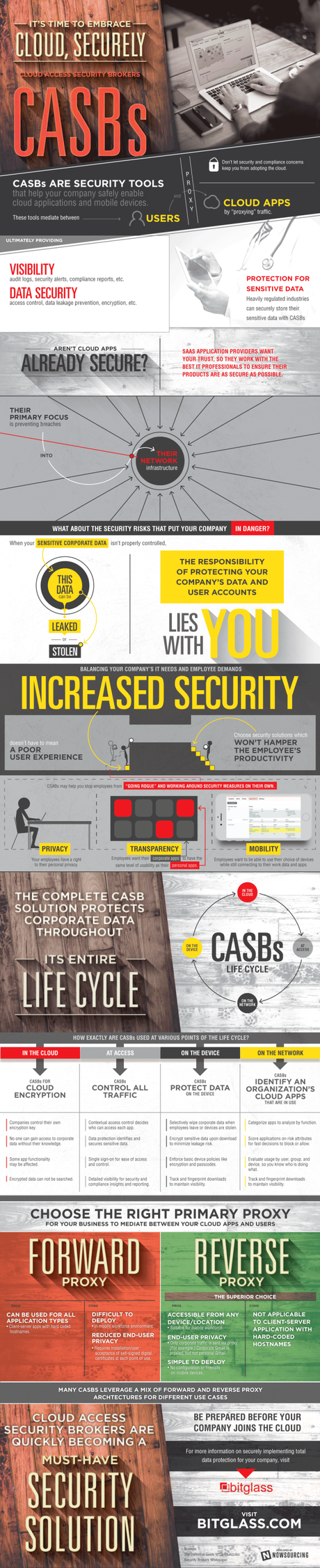 en.paperblog.com
en.paperblog.com layer
Is My Data Safe In The Clouds?Cloud Computing And Related Security
 securereading.com
securereading.com clouds securereading
Top 5 Best Practices For Cloud Security - Infosecurity Magazine
 www.infosecurity-magazine.com
www.infosecurity-magazine.com infosecurity
Five Best Practices For Cloud Security - United States Cybersecurity
 www.uscybersecurity.net
www.uscybersecurity.net practices companies
Best Practices For Cloud Security
 www.slideshare.net
www.slideshare.net cloud slideshare practices security
8 security benefits of cloud computing. Is my data safe in the clouds?cloud computing and related security. Best practices for cloud security
if you are looking "id":696,"keyword_id":33,"name":"cloud data security best practices","scraped_at":"2022-12-16 03:31:23","created_at":"2022-12-16T03:31:23.000000Z","updated_at":"2022-12-16T03:31:23.000000Z","images":["id":5708,"keyword_id":696,"url":"https:\/\/www.uscybersecurity.net\/wp-content\/uploads\/2021\/02\/5-Best-Practices-for-Cloud-Security-Final.jpg","link":"https:\/\/www.uscybersecurity.net\/csmag\/five-best-practices-for-cloud-security\/","title":"Five Best Practices for Cloud Security - United States Cybersecurity","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.XJQJLu8dVCgbDzSzgum_-gHaDY&pid=15.1","size":"768 x 351 \u00b7 jpeg","desc":"practices companies","filetype":"jpg","width":768,"height":351,"domain":"www.uscybersecurity.net","created_at":null,"updated_at":null,"id":5709,"keyword_id":696,"url":"https:\/\/assets.infosecurity-magazine.com\/webpage\/tw\/84cc4930-9880-4f52-b451-a22539fccde1.png","link":"https:\/\/www.infosecurity-magazine.com\/magazine-features\/top-5-best-practices-for-cloud\/","title":"Top 5 Best Practices for Cloud Security - Infosecurity Magazine","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.R6hSSQTA9gfMHuhGaxVEkwAAAA&pid=15.1","size":"280 x 157 \u00b7 png","desc":"infosecurity","filetype":"png","width":280,"height":157,"domain":"www.infosecurity-magazine.com","created_at":null,"updated_at":null,"id":5710,"keyword_id":696,"url":"https:\/\/i.pinimg.com\/originals\/c3\/5f\/24\/c35f24221c2a9cf691dd045101b49023.jpg","link":"https:\/\/www.pinterest.com\/pin\/818881144726250048\/","title":"8 security benefits of cloud computing ,"id":5711,"keyword_id":696,"url":"https:\/\/image.slidesharecdn.com\/intelitvirtualizationcloudsecurityslideshow-120624233500-phpapp01\/95\/best-practices-for-cloud-security-12-728.jpg?cb=1340581180","link":"https:\/\/www.slideshare.net\/ITatIntel\/intel-it-virtualization-cloudsecurityslideshow","title":"Best Practices for Cloud Security","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.A75uJAcKqRSWQIutYMGW5wHaFj&pid=15.1","size":"728 x 546 \u00b7 jpeg","desc":"","filetype":"jpg","width":728,"height":546,"domain":"www.slideshare.net","created_at":null,"updated_at":null,"id":5712,"keyword_id":696,"url":"https:\/\/securereading.com\/wp-content\/uploads\/2016\/09\/cloud-computing_1_2017-300x225.png","link":"https:\/\/securereading.com\/is-my-data-safe-in-the-clouds\/","title":"Is My Data Safe in the Clouds?Cloud Computing and Related Security","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.T9nh-n-Cki7vDsD82Bi5HQAAAA&pid=15.1","size":"300 x 225 \u00b7 png","desc":"clouds securereading","filetype":"png","width":300,"height":225,"domain":"securereading.com","created_at":null,"updated_at":null,"id":5713,"keyword_id":696,"url":"https:\/\/www.h-x.technology\/wp-content\/uploads\/2020\/11\/Cloud-Infograf-1.jpg","link":"https:\/\/www.h-x.technology\/services\/cloud-security-implementation","title":"Implementation of cloud security - H-X Technologies","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.aEyI9mYuC3Ci84hHsq406QHaEP&pid=15.1","size":"600 x 344 \u00b7 jpeg","desc":"","filetype":"jpg","width":600,"height":344,"domain":"www.h-x.technology","created_at":null,"updated_at":null,"id":5714,"keyword_id":696,"url":"https:\/\/m5.paperblog.com\/i\/102\/1023758\/secure-your-data-on-the-cloud-L-ozKkoZ.png","link":"https:\/\/en.paperblog.com\/secure-your-data-on-the-cloud-1023758\/","title":"Secure Your Data On The Cloud - Paperblog","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.drzXXttDfwtQjADvbiFxBAAAAA&pid=15.1","size":"460 x 2252 \u00b7 png","desc":"layer","filetype":"png","width":460,"height":2252,"domain":"en.paperblog.com","created_at":null,"updated_at":null,"id":5715,"keyword_id":696,"url":"https:\/\/www.connectria.com\/wp-content\/uploads\/2019\/06\/Cloud_Computing_data_Centers.jpeg","link":"https:\/\/www.connectria.com\/blog\/how-are-cloud-computing-and-data-centers-related\/","title":"How Are Cloud Computing and Data Centers Related? ,"id":5716,"keyword_id":696,"url":"https:\/\/image.slidesharecdn.com\/intelitvirtualizationcloudsecurityslideshow-120624233500-phpapp01\/95\/best-practices-for-cloud-security-1-728.jpg?cb=1340581180","link":"https:\/\/www.slideshare.net\/ITatIntel\/intel-it-virtualization-cloudsecurityslideshow","title":"Best Practices for Cloud Security","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.2Pf788-B9Qx9BAa9_Ziq1AHaFj&pid=15.1","size":"728 x 546 \u00b7 jpeg","desc":"cloud slideshare practices security","filetype":"jpg","width":728,"height":546,"domain":"www.slideshare.net","created_at":null,"updated_at":null] this site you are coming to the right page. Contains many images about cloud data security best practices Clouds securereading. Don't forget to bookmark this page for future reference or share to facebook / twitter if you like this page.
No comments:
Post a Comment