If you are searching about Researchers steal secret RSA encryption keys in Amazon’s cloud you've came to the right web. We have 8 Pics about Researchers steal secret RSA encryption keys in Amazon’s cloud like Understanding the cloud, Homomorphic Encryption for Beginners: A Practical Guide (Part 1) | by and also Homomorphic Encryption for Beginners: A Practical Guide (Part 1) | by. Here it is:
Researchers Steal Secret RSA Encryption Keys In Amazon’s Cloud
 www.networkworld.com
www.networkworld.com steal stolen secret laptops cloud researchers keys laptop thief theft encryption rsa crypto em got burglar office thinkstock most
Cloud Round Icons - Vector Stencils Library
process icon vector round icons library stencils cloud midwest streams
What Is Social Engineering? - Security - SDxCentral
 www.sdxcentral.com
www.sdxcentral.com sdxcentral
Homomorphic Encryption For Beginners: A Practical Guide (Part 1) | By
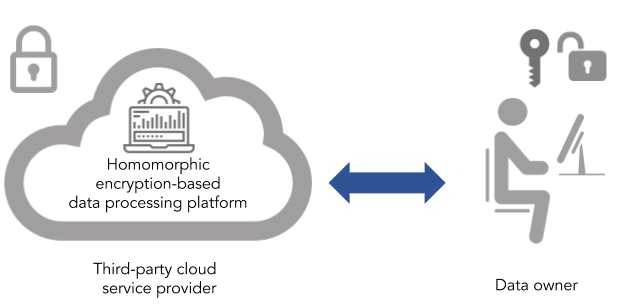 medium.com
medium.com encryption homomorphic
TikTok’s UK Presence Threatened As Gov Considers Restrictions | IT PRO
 www.itpro.co.uk
www.itpro.co.uk itpro
All Zoom Users Get End-to-end Encryption (E2EE) Option Next Week - Help
 www.helpnetsecurity.com
www.helpnetsecurity.com zoom end option
UK SMS Text Message Use Fell For First Time In 2013 | IT PRO
 www.itpro.co.uk
www.itpro.co.uk sms message text itpro
Understanding The Cloud
 betanews.com
betanews.com cloud computing man clouds saas move why understanding hand pstn voip office applications service accountant hosted legacy humans computers middle
Encryption homomorphic. Sms message text itpro. What is social engineering?
if you are looking "id":210,"keyword_id":32,"name":"Cloud Encryption","scraped_at":"2022-12-16 03:31:19","created_at":"2022-12-16T03:31:19.000000Z","updated_at":"2022-12-16T03:31:19.000000Z","images":["id":1289,"keyword_id":210,"url":"https:\/\/betanews.com\/wp-content\/uploads\/2014\/04\/man-in-cloud-e1464621647235.jpg","link":"https:\/\/betanews.com\/2014\/10\/31\/understanding-the-cloud\/","title":"Understanding the cloud","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.vXCv5Yunr0iE4NfH7uOtKAHaEn&pid=15.1","size":"640 x 399 \u00b7 jpeg","desc":"cloud computing man clouds saas move why understanding hand pstn voip office applications service accountant hosted legacy humans computers middle","filetype":"jpg","width":640,"height":399,"domain":"betanews.com","created_at":null,"updated_at":null, by","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.in_mHrOeYcN6VVTNPwscpwHaDs&pid=15.1","size":"618 x 308 \u00b7 png","desc":"encryption homomorphic","filetype":"png","width":618,"height":308,"domain":"medium.com","created_at":null,"updated_at":null,"id":1291,"keyword_id":210,"url":"https:\/\/img.helpnetsecurity.com\/wp-content\/uploads\/2020\/10\/15141706\/zoom_end-to-end.jpg","link":"https:\/\/www.helpnetsecurity.com\/2020\/10\/15\/zoom-e2ee-end-to-end-encryption\/","title":"All Zoom users get end-to-end encryption (E2EE) option next week - Help","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.aa-Kl9i3PHyVnbZMmyHMjAHaEk&pid=15.1","size":"1000 x 618 \u00b7 jpeg","desc":"zoom end option","filetype":"jpg","width":1000,"height":618,"domain":"www.helpnetsecurity.com","created_at":null,"updated_at":null,"id":1292,"keyword_id":210,"url":"https:\/\/conceptdraw.com\/a155c4\/p138\/preview\/640\/pict--process-cloud-round-icons-vector-stencils-library","link":"https:\/\/conceptdraw.com\/a155c4\/p138\/preview\/640","title":"Cloud round icons - Vector stencils library","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.xANce7tuJgCsxpo2DYkU4gHaHa&pid=15.1","size":"640 x 640 \u00b7 png","desc":"process icon vector round icons library stencils cloud midwest streams","filetype":"png","width":640,"height":640,"domain":"conceptdraw.com","created_at":null,"updated_at":null,"id":1293,"keyword_id":210,"url":"https:\/\/www.sdxcentral.com\/wp-content\/uploads\/2020\/08\/What-is-Social-Engineering_.jpg","link":"https:\/\/www.sdxcentral.com\/security\/definitions\/what-is-social-engineering\/","title":"What is Social Engineering? - Security - SDxCentral","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.SEDdTFpaXxKawTpCvI7QbwHaDt&pid=15.1","size":"1200 x 600 \u00b7 jpeg","desc":"sdxcentral","filetype":"jpg","width":1200,"height":600,"domain":"www.sdxcentral.com","created_at":null,"updated_at":null,"id":1294,"keyword_id":210,"url":"https:\/\/media.itpro.co.uk\/image\/upload\/v1570812409\/itpro\/images\/dir_154\/it_photo_77117.jpg","link":"https:\/\/www.itpro.co.uk\/apps\/21383\/uk-sms-text-message-use-fell-for-first-time-in-2013","title":"UK SMS text message use fell for first time in 2013 ,"id":1295,"keyword_id":210,"url":"https:\/\/media.itpro.co.uk\/image\/upload\/v1598526814\/itpro\/shutterstock_tiktok_london.jpg","link":"https:\/\/www.itpro.co.uk\/business\/policy-legislation\/356903\/tiktoks-uk-presence-threatened-as-gov-considers-restrictions","title":"TikTok\u2019s UK presence threatened as gov considers restrictions ,"id":1296,"keyword_id":210,"url":"https:\/\/images.techhive.com\/images\/article\/2015\/08\/steal-100606619-primary.idge.jpg","link":"http:\/\/www.networkworld.com\/article\/2989757\/cloud-security\/researchers-steal-secret-rsa-encryption-keys-in-amazon-s-cloud.html","title":"Researchers steal secret RSA encryption keys in Amazon\u2019s cloud","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.BbpWa_J4WiNc7d0TswT91wHaE7&pid=15.1","size":"620 x 413 \u00b7 jpeg","desc":"steal stolen secret laptops cloud researchers keys laptop thief theft encryption rsa crypto em got burglar office thinkstock most","filetype":"jpg","width":620,"height":413,"domain":"www.networkworld.com","created_at":null,"updated_at":null] this site you are coming to the right page. Contains many images about Cloud Encryption Cloud computing man clouds saas move why understanding hand pstn voip office applications service accountant hosted legacy humans computers middle. Don't forget to bookmark this page for future reference or share to facebook / twitter if you like this page.
No comments:
Post a Comment