If you are searching about Data Security Statistics - Understanding cloud data security risks you've visit to the right page. We have 9 Pics about Data Security Statistics - Understanding cloud data security risks like More than 2.5 billion records stolen or compromised in 2017 | Business Wire, Safety Measures to Evade Cloud Security Threats - CloudReviews | Cloud and also [Infographic] Top Five Cloud Security Threats | Mindsight. Here you go:
Data Security Statistics - Understanding Cloud Data Security Risks
 www.access-smart.com
www.access-smart.com security cloud computing data challenges issues risks related threats infrastructure clouds statistics key services safe sound why secure oep perez
Top Cyber Security Threats In 2021 | Mindcore
 mind-core.com
mind-core.com threats cybersecurity worst
More Than 2.5 Billion Records Stolen Or Compromised In 2017 | Business Wire
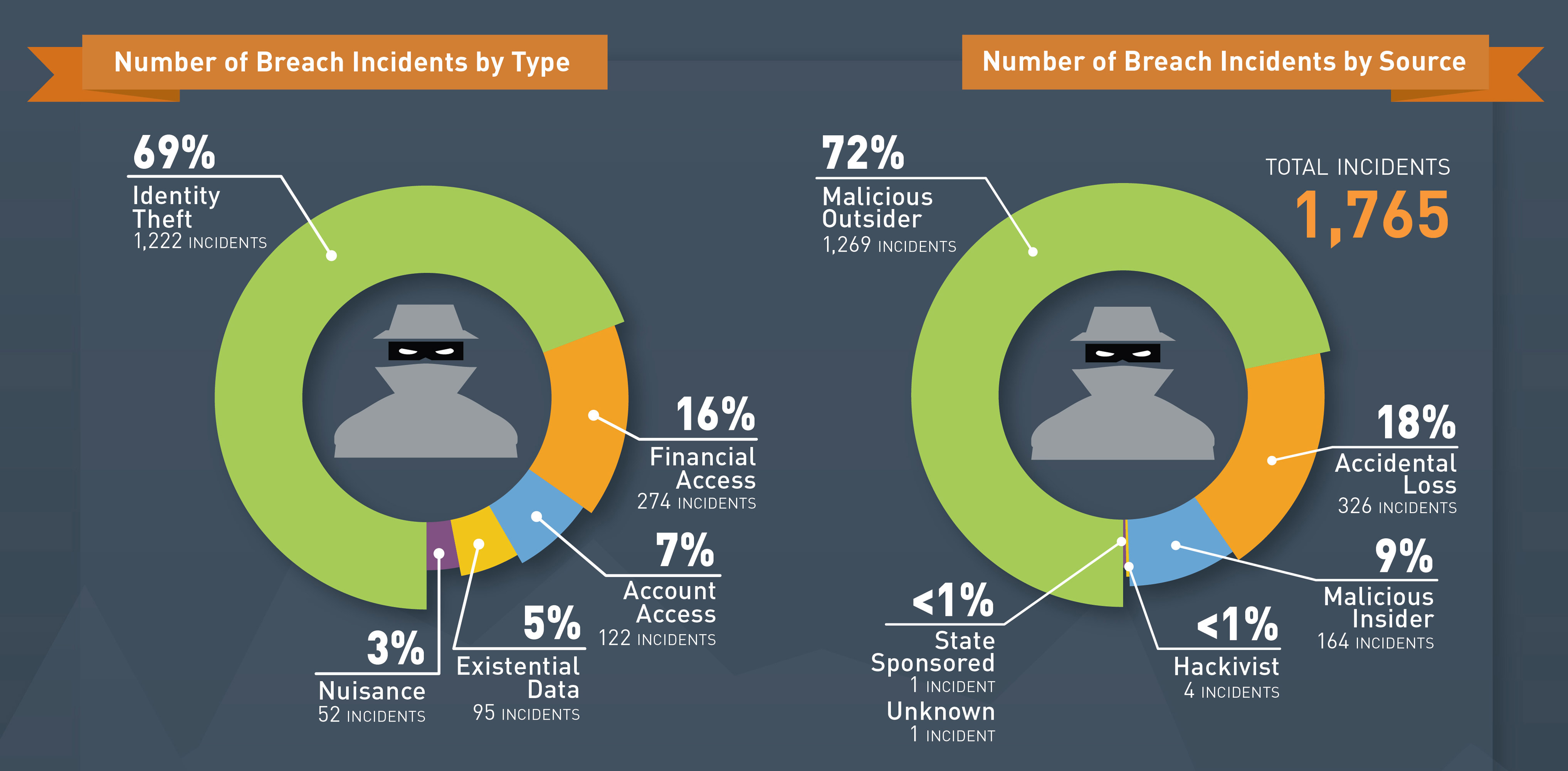 www.businesswire.com
www.businesswire.com breach incidents gemalto threats compromised comprometidos millones robados multipress aangetast gestolen miljard businesswire
Infographic - Cloud Security Concerns
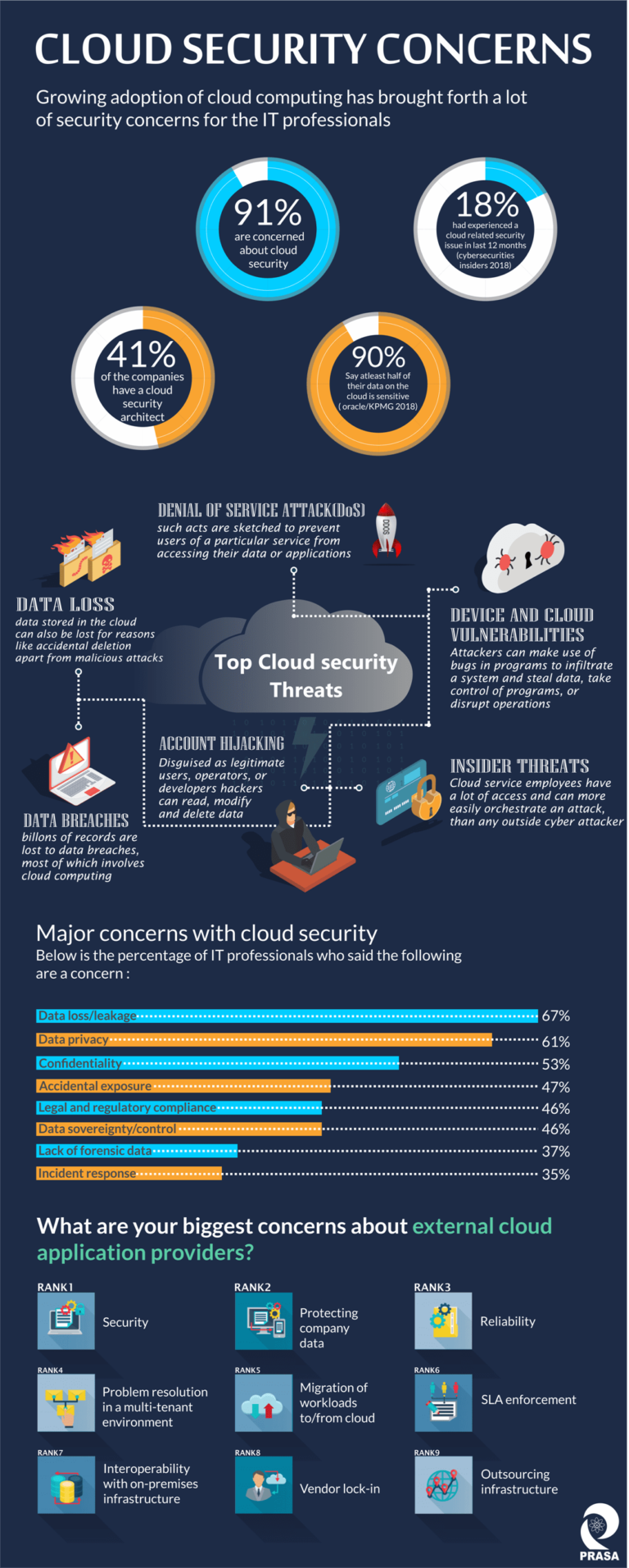 prasa-pl.com
prasa-pl.com concerns prasa concern
[Infographic] Top Five Cloud Security Threats | Mindsight
![[Infographic] Top Five Cloud Security Threats | Mindsight](https://gomindsight.com/wp-content/uploads/2017/05/Top-5-Cloud-Security-Threats-Infographic.png) gomindsight.com
gomindsight.com threats
Cloud Security To Be One Of The Biggest Challenges For 2016
:max_bytes(150000):strip_icc()/cloudsecurity-568596763df78ccc15e67d16.jpg) www.lifewire.com
www.lifewire.com cloud security issues challenges computing tips data threats securing solution privacy mobile device prevention attacks lab
Fig. Cloud Computing Security Threats | Download Scientific Diagram
 www.researchgate.net
www.researchgate.net Discover The Cloud Security Threats In 2018 - Cisco Community
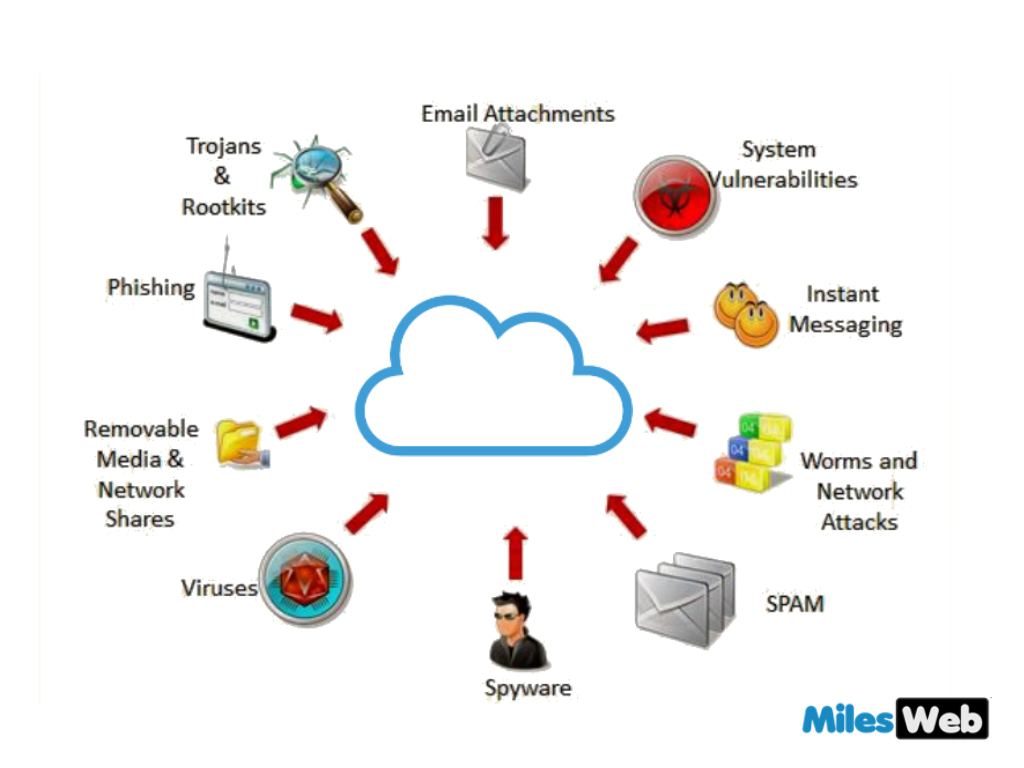 community.cisco.com
community.cisco.com cloud security threats computing discover cisco community
Safety Measures To Evade Cloud Security Threats - CloudReviews | Cloud
cloud threats security computing cloudhq measures evade safety properly migration happen process should
Cloud security issues challenges computing tips data threats securing solution privacy mobile device prevention attacks lab. Safety measures to evade cloud security threats. Cloud security to be one of the biggest challenges for 2016
if you are looking "id":701,"keyword_id":33,"name":"cloud data security threats","scraped_at":"2022-12-16 03:31:23","created_at":"2022-12-16T03:31:23.000000Z","updated_at":"2022-12-16T03:31:23.000000Z","images":[ Business Wire","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.MK6eK_f4rluBy6zxQwDeVAHaDo&pid=15.1","size":"4069 x 2000 \u00b7 jpeg","desc":"breach incidents gemalto threats compromised comprometidos millones robados multipress aangetast gestolen miljard businesswire","filetype":"jpg","width":4069,"height":2000,"domain":"www.businesswire.com","created_at":null,"updated_at":null,"id":5745,"keyword_id":701,"url":"http:\/\/www.cloudreviews.com\/blog\/wp-content\/uploads\/2012\/10\/Untitled-13.jpg","link":"http:\/\/www.cloudreviews.com\/blog\/cloud-security-threats","title":"Safety Measures to Evade Cloud Security Threats - CloudReviews ,"id":5746,"keyword_id":701,"url":"https:\/\/www.access-smart.com\/wp-content\/uploads\/2011\/12\/cloudsecurity.png","link":"https:\/\/www.access-smart.com\/data-security\/cloud\/","title":"Data Security Statistics - Understanding cloud data security risks","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.0WUjjUKDylyvpTqiNi7y0wAAAA&pid=15.1","size":"404 x 323 \u00b7 png","desc":"security cloud computing data challenges issues risks related threats infrastructure clouds statistics key services safe sound why secure oep perez","filetype":"png","width":404,"height":323,"domain":"www.access-smart.com","created_at":null,"updated_at":null,"id":5747,"keyword_id":701,"url":"https:\/\/www.researchgate.net\/profile\/Haitam_Laarabi\/publication\/233781365\/figure\/download\/fig12\/AS:700925857501185@1544125155738\/Fig-Cloud-Computing-Security-Threats.jpg","link":"https:\/\/www.researchgate.net\/figure\/Fig-Cloud-Computing-Security-Threats_fig12_233781365","title":"Fig. Cloud Computing Security Threats ,"id":5748,"keyword_id":701,"url":"https:\/\/prasa-pl.com\/wp-content\/uploads\/2019\/04\/cloud-security-infographic-compressed-min-768x1913.png","link":"https:\/\/prasa-pl.com\/blog\/infographic-cloud-security-concerns\/","title":"Infographic - Cloud Security Concerns","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.G2OZgNmwVowPAaJ1GvrJ3gHaSc&pid=15.1","size":"768 x 1913 \u00b7 png","desc":"concerns prasa concern","filetype":"png","width":768,"height":1913,"domain":"prasa-pl.com","created_at":null,"updated_at":null,"id":5749,"keyword_id":701,"url":"https:\/\/mind-core.com\/wp-content\/uploads\/2021\/08\/AdobeStock_189351452.jpeg","link":"https:\/\/mind-core.com\/blogs\/cybersecurity\/top-cyber-security-threats-in-2021\/","title":"Top Cyber Security Threats in 2021 ,"id":5750,"keyword_id":701,"url":"https:\/\/community.cisco.com\/legacyfs\/online\/fusion\/116573_Cloud Security Threats.jpg","link":"https:\/\/community.cisco.com\/t5\/security-blogs\/discover-the-cloud-security-threats-in-2018\/ba-p\/3664430","title":"Discover the Cloud Security Threats in 2018 - Cisco Community","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.-W0tZJI0m7486gdsVDYNXgHaFj&pid=15.1","size":"1024 x 768 \u00b7 jpeg","desc":"cloud security threats computing discover cisco community","filetype":"jpg","width":1024,"height":768,"domain":"community.cisco.com","created_at":null,"updated_at":null,"id":5751,"keyword_id":701,"url":"https:\/\/www.lifewire.com\/thmb\/eZcLp9JKwukDwyOIG3Uzcnipu8o=\/768x0\/filters:no_upscale():max_bytes(150000):strip_icc()\/cloudsecurity-568596763df78ccc15e67d16.jpg","link":"https:\/\/www.lifewire.com\/cloud-mobile-device-security-challenges-3473908","title":"Cloud Security to be One of the Biggest Challenges for 2016","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.KIztE8hh98MuRPu8rGe6aAHaEs&pid=15.1","size":"716 x 454 \u00b7 jpeg","desc":"cloud security issues challenges computing tips data threats securing solution privacy mobile device prevention attacks lab","filetype":"jpg","width":716,"height":454,"domain":"www.lifewire.com","created_at":null,"updated_at":null,"id":5752,"keyword_id":701,"url":"https:\/\/gomindsight.com\/wp-content\/uploads\/2017\/05\/Top-5-Cloud-Security-Threats-Infographic.png","link":"https:\/\/gomindsight.com\/insights\/blog\/infographic-top-five-cloud-security-threats\/","title":"[Infographic] Top Five Cloud Security Threats ] this site you are coming to the right page. Contains many images about cloud data security threats Cloud security issues challenges computing tips data threats securing solution privacy mobile device prevention attacks lab. Don't forget to bookmark this page for future reference or share to facebook / twitter if you like this page.
No comments:
Post a Comment