If you are searching about SSL Encryption Must for Cloud Computing Security you've visit to the right web. We have 9 Pics about SSL Encryption Must for Cloud Computing Security like 4 key data security challenges in cloud computing - Techiexpert.com, data security in cloud| trends in cloud security | Cloud Computing and also SSL Encryption Must for Cloud Computing Security. Here it is:
SSL Encryption Must For Cloud Computing Security
 www.rapidsslonline.com
www.rapidsslonline.com cloud computing security encryption data technology network service enterprise computer aspect mandatory delivery system examples storage
Why Invest In Data Security In Cloud Computing | IT Briefcase
cloud security computing data technology why business investment inquire owners starting days
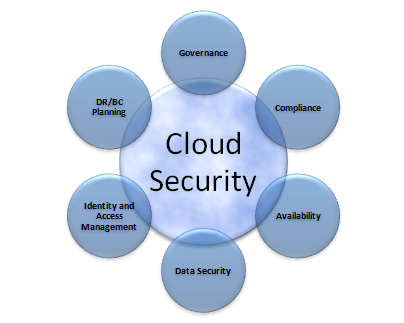
4 Key Data Security Challenges In Cloud Computing - Techiexpert.com
 www.techiexpert.com
www.techiexpert.com cloud security computing data challenges key applications enterprise grade snp techiexpert secure
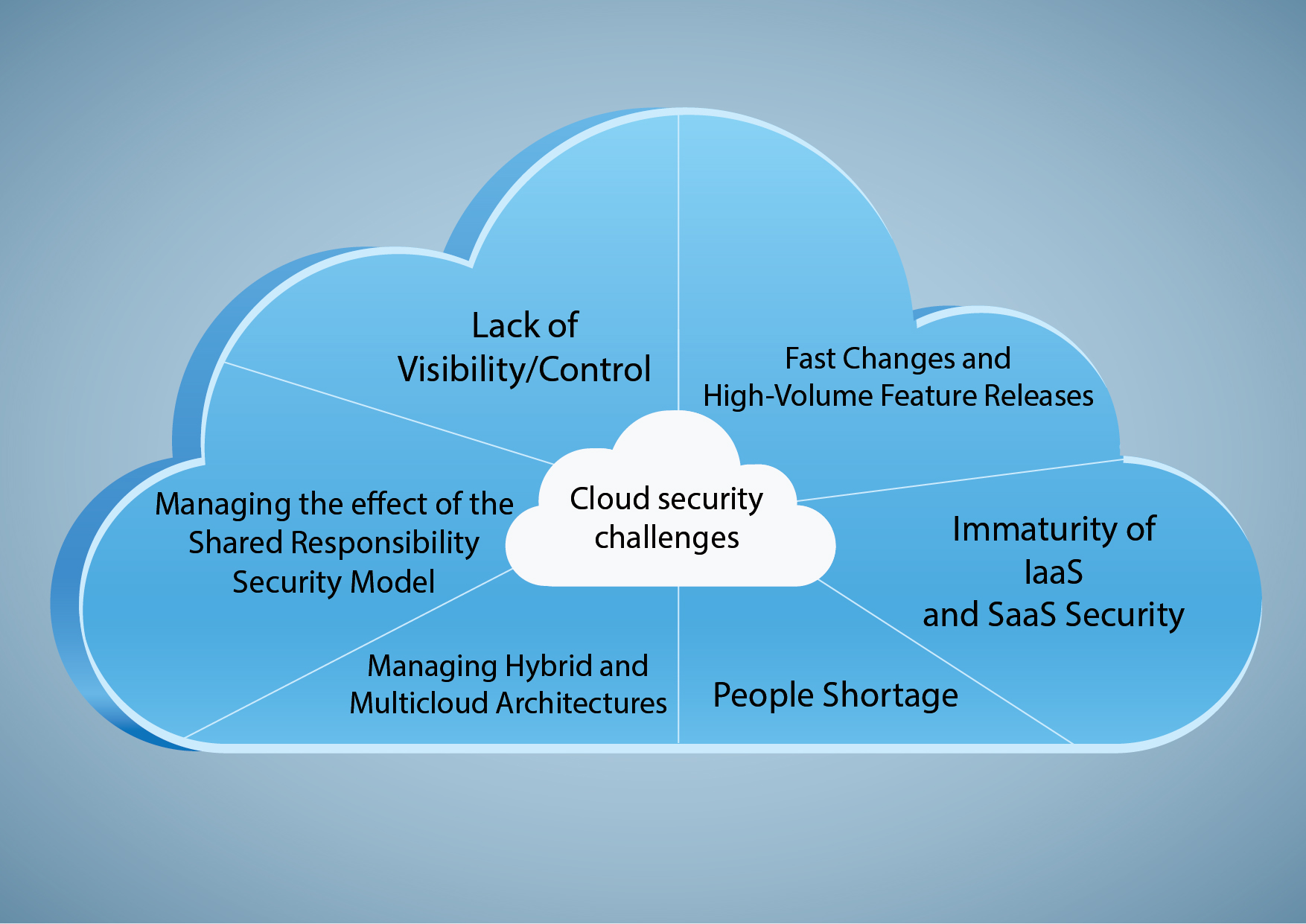
Data Security Statistics - Understanding Cloud Data Security Risks
 www.access-smart.com
www.access-smart.com security cloud computing data challenges issues risks related threats infrastructure clouds statistics key services safe sound why secure oep perez
CLOUD COMPUTING SECURITY ISSUES, CHALLENGES AND SOLUTION - E2MATRIX
cloud security issues challenges computing tips data threats securing solution privacy attacks mobile prevention device lab
Data Security In Cloud| Trends In Cloud Security | Cloud Computing
 www.suntechnologies.com
www.suntechnologies.com lack computing visibility suntechnologies
Cloud & Mobile Deployments Are The Weakest Links In Enterprise Networks
 www.dynamicciso.com
www.dynamicciso.com cloud enterprise security report networks point check deployments weakest mobile links infrastructure threat instalment third published its
How To Ensure Data Security In Cloud Computing - IndustryWired
 industrywired.com
industrywired.com computing industrywired
Data Security In Cloud Computing: Key Components
 blog.netwrix.com
blog.netwrix.com cloud
Cloud security issues challenges computing tips data threats securing solution privacy attacks mobile prevention device lab. Ssl encryption must for cloud computing security. Data security in cloud| trends in cloud security
if you are looking "id":694,"keyword_id":33,"name":"data security in cloud computing","scraped_at":"2022-12-16 03:31:23","created_at":"2022-12-16T03:31:23.000000Z","updated_at":"2022-12-16T03:31:23.000000Z","images":["id":5849,"keyword_id":694,"url":"https:\/\/www.techiexpert.com\/wp-content\/uploads\/2019\/05\/Data-security-challenges-in-cloud-computing.jpg","link":"https:\/\/www.techiexpert.com\/4-key-data-security-challenges-in-cloud-computing\/","title":"4 key data security challenges in cloud computing - Techiexpert.com","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.uAFCadLpn0aD4O8ZcD9JbgHaES&pid=15.1","size":"1024 x 594 \u00b7 jpeg","desc":"cloud security computing data challenges key applications enterprise grade snp techiexpert secure","filetype":"jpg","width":1024,"height":594,"domain":"www.techiexpert.com","created_at":null,"updated_at":null, trends in cloud security ,"id":5851,"keyword_id":694,"url":"https:\/\/www.rapidsslonline.com\/blog\/wp-content\/uploads\/2014\/11\/cloud-computing-security-with-ssl-encryption1.png","link":"https:\/\/www.rapidsslonline.com\/blog\/ssl-encryption-mandatory-aspect-cloud-computing-security","title":"SSL Encryption Must for Cloud Computing Security","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.OHQbvSGiMFXM_mqeWXkjfQHaGh&pid=15.1","size":"920 x 810 \u00b7 png","desc":"cloud computing security encryption data technology network service enterprise computer aspect mandatory delivery system examples storage","filetype":"png","width":920,"height":810,"domain":"www.rapidsslonline.com","created_at":null,"updated_at":null,"id":5852,"keyword_id":694,"url":"https:\/\/industrywired.b-cdn.net\/wp-content\/uploads\/2020\/01\/How_to-Ensure-Data-Security-in-Cloud-Computing.jpg","link":"https:\/\/industrywired.com\/how-to-ensure-data-security-in-cloud-computing\/","title":"How to Ensure Data Security in Cloud Computing - IndustryWired","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.hvKfFgzdEWYXyKPfBuTZUgHaEL&pid=15.1","size":"1200 x 677 \u00b7 jpeg","desc":"computing industrywired","filetype":"jpg","width":1200,"height":677,"domain":"industrywired.com","created_at":null,"updated_at":null, IT Briefcase","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.9z9O3VEB60B2O_skhrgEHAHaFb&pid=15.1","size":"2000 x 1468 \u00b7 jpeg","desc":"cloud security computing data technology why business investment inquire owners starting days","filetype":"jpg","width":2000,"height":1468,"domain":"www.itbriefcase.net","created_at":null,"updated_at":null,"id":5854,"keyword_id":694,"url":"http:\/\/www.e2matrix.com\/blog\/wp-content\/uploads\/2017\/10\/2.jpg","link":"http:\/\/www.e2matrix.com\/blog\/2017\/10\/13\/cloud-computing-security-issues-challenges-and-solution\/","title":"CLOUD COMPUTING SECURITY ISSUES, CHALLENGES AND SOLUTION - E2MATRIX","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.EdGWA0H7zbeN20n6z8W_8gHaEs&pid=15.1","size":"716 x 454 \u00b7 jpeg","desc":"cloud security issues challenges computing tips data threats securing solution privacy attacks mobile prevention device lab","filetype":"jpg","width":716,"height":454,"domain":"www.e2matrix.com","created_at":null,"updated_at":null,"id":5855,"keyword_id":694,"url":"https:\/\/www.access-smart.com\/wp-content\/uploads\/2011\/12\/cloudsecurity.png","link":"https:\/\/www.access-smart.com\/data-security\/cloud\/","title":"Data Security Statistics - Understanding cloud data security risks","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.0WUjjUKDylyvpTqiNi7y0wAAAA&pid=15.1","size":"404 x 323 \u00b7 png","desc":"security cloud computing data challenges issues risks related threats infrastructure clouds statistics key services safe sound why secure oep perez","filetype":"png","width":404,"height":323,"domain":"www.access-smart.com","created_at":null,"updated_at":null,"id":5856,"keyword_id":694,"url":"https:\/\/dynamicciso.com\/wp-content\/uploads\/2019\/02\/cloud-security.jpg","link":"https:\/\/www.dynamicciso.com\/cloud-mobile-deployments-are-the-weakest-links-in-enterprise-networks-check-point-report\/","title":"Cloud & Mobile Deployments Are the Weakest Links in Enterprise Networks","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.j3T06chV0yCFsJYczEC_FgHaFD&pid=15.1","size":"2095 x 1431 \u00b7 jpeg","desc":"cloud enterprise security report networks point check deployments weakest mobile links infrastructure threat instalment third published its","filetype":"jpg","width":2095,"height":1431,"domain":"www.dynamicciso.com","created_at":null,"updated_at":null,"id":5857,"keyword_id":694,"url":"https:\/\/cdn-blog.netwrix.com\/wp-content\/uploads\/2020\/07\/Data-Security-in-Cloud-Computing.jpg","link":"https:\/\/blog.netwrix.com\/2020\/07\/02\/cloud-data-security\/","title":"Data Security in Cloud Computing: Key Components","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.aIngw4cD0yMpuGGJvO8i9wHaB_&pid=15.1","size":"1120 x 301 \u00b7 jpeg","desc":"cloud","filetype":"jpg","width":1120,"height":301,"domain":"blog.netwrix.com","created_at":null,"updated_at":null] this site you are coming to the right page. Contains many images about data security in cloud computing Data security in cloud computing: key components. Don't forget to bookmark this page for future reference or share to facebook / twitter if you like this page.
No comments:
Post a Comment