If you are looking for Lifecycle Images and Stock Photos. 3,903 Lifecycle photography and you've visit to the right web. We have 9 Pics about Lifecycle Images and Stock Photos. 3,903 Lifecycle photography and like Securosis - Blog - Article, Data Security Lifecycle 2.0 and also A Framework for Cloud Computing. Here it is:
Lifecycle Images And Stock Photos. 3,903 Lifecycle Photography And
 www.canstockphoto.com
www.canstockphoto.com lifecycle vaeenma security data royalty cycle development system
Data Security Lifecycle 2.0
 www.mayurpahwa.com
www.mayurpahwa.com lifecycle
A Framework For Cloud Computing
cloud framework computing characteristics platform
(PDF) A Survey On Top Security Threats In Cloud Computing
 www.researchgate.net
www.researchgate.net computing cloud data survey cycle threats security
Securosis - Blog - Article
 securosis.com
securosis.com lifecycle
Cloud Computing - Data Security Lifecycle In The Cloud
 www.slideshare.net
www.slideshare.net lifecycle
Securosis - Blog - Article
 securosis.com
securosis.com security data lifecycle management protection cloud database storage centric pragmatic typical needs reflect virtual private
Protecting Cloud Data Throughout Its Lifecycle - Security Boulevard
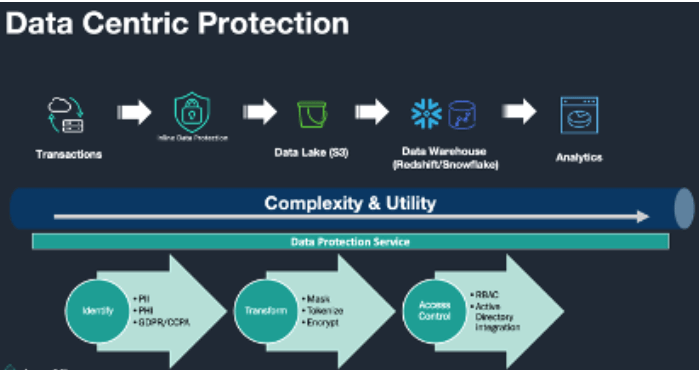 securityboulevard.com
securityboulevard.com lifecycle
Agile, Scrum, Kanban, Architecture,: Information Lifecycle For Data
 agileanswer.blogspot.com
agileanswer.blogspot.com lifecycle data security stages cloud management architecture follows subtle hides typically following
Cloud computing. Lifecycle vaeenma security data royalty cycle development system. Cloud framework computing characteristics platform
if you are looking "id":698,"keyword_id":33,"name":"cloud data security lifecycle","scraped_at":"2022-12-16 03:31:23","created_at":"2022-12-16T03:31:23.000000Z","updated_at":"2022-12-16T03:31:23.000000Z","images":["id":5699,"keyword_id":698,"url":"https:\/\/cdn.securosis.com\/assets\/library\/main\/Pragmatic_Data_Security-_Data_Protection_DecisiionsV2.008_.png","link":"http:\/\/securosis.com\/blog\/musings-on-data-security-in-the-cloud","title":"Securosis - Blog - Article","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.0eAQZgYsPDWC7PWhGr8RMwHaFj&pid=15.1","size":"1024 x 768 \u00b7 png","desc":"security data lifecycle management protection cloud database storage centric pragmatic typical needs reflect virtual private","filetype":"png","width":1024,"height":768,"domain":"securosis.com","created_at":null,"updated_at":null,"id":5700,"keyword_id":698,"url":"https:\/\/1.bp.blogspot.com\/-sEM73_lB8kQ\/YMXYosI94oI\/AAAAAAAAC68\/ntmoSESwG_g3m2Ts4FG33GNRNBT_-Gs3gCNcBGAsYHQ\/s16000\/DLS2.png","link":"https:\/\/www.mayurpahwa.com\/2021\/06\/data-security-lifecycle-20.html","title":"Data Security Lifecycle 2.0","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.nz2BN4_7j8_AqEN6sIe6LgHaEK&pid=15.1","size":"1280 x 720 \u00b7 png","desc":"lifecycle","filetype":"png","width":1280,"height":720,"domain":"www.mayurpahwa.com","created_at":null,"updated_at":null,"id":5701,"keyword_id":698,"url":"https:\/\/image.slidesharecdn.com\/kpmgdatasecuritylifecycleinthecloud-100317164915-phpapp01\/95\/cloud-computing-data-security-lifecycle-in-the-cloud-7-728.jpg?cb=1268844681","link":"http:\/\/www.slideshare.net\/eburon\/kpmg-data-security-lifecycle-in-the-cloud","title":"Cloud Computing - Data Security Lifecycle In The Cloud","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.V5uVcIuu7ejaKWeo9eaczwHaFu&pid=15.1","size":"942 x 728 \u00b7 jpeg","desc":"lifecycle","filetype":"jpg","width":942,"height":728,"domain":"www.slideshare.net","created_at":null,"updated_at":null,"id":5702,"keyword_id":698,"url":"https:\/\/baffle.io\/wp-content\/uploads\/2021\/05\/Screen-Shot-2021-05-10-at-3.11.20-PM.png","link":"https:\/\/securityboulevard.com\/2021\/05\/protecting-cloud-data-throughout-its-lifecycle\/","title":"Protecting Cloud Data Throughout Its Lifecycle - Security Boulevard","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.hBy_DWzszKFeAfXGk5BBOwHaD6&pid=15.1","size":"700 x 370 \u00b7 png","desc":"lifecycle","filetype":"png","width":700,"height":370,"domain":"securityboulevard.com","created_at":null,"updated_at":null,"id":5703,"keyword_id":698,"url":"https:\/\/www.researchgate.net\/publication\/273950623\/figure\/fig1\/AS:294693821796353@1447271890094\/Data-life-cycle-in-cloud-computing_Q320.jpg","link":"https:\/\/www.researchgate.net\/publication\/273950623_A_survey_on_top_security_threats_in_cloud_computing","title":"(PDF) A survey on top security threats in cloud computing","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.41HNKyU5mF9vI1HP6dHVSgAAAA&pid=15.1","size":"320 x 320 \u00b7 jpeg","desc":"computing cloud data survey cycle threats security","filetype":"jpg","width":320,"height":320,"domain":"www.researchgate.net","created_at":null,"updated_at":null,"id":5704,"keyword_id":698,"url":"http:\/\/4.bp.blogspot.com\/-fmba9-4GIBA\/Tjn2963Nb_I\/AAAAAAAAAZU\/17UwnnlwGdo\/s640\/InforamtionLifecycle.JPG","link":"http:\/\/agileanswer.blogspot.com\/2011\/08\/information-lifecycle-for-data-security.html","title":"Agile, Scrum, Kanban, Architecture,: Information Lifecycle for Data","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.S7RX1a4R_Epxf3OyLzb05AHaEe&pid=15.1","size":"484 x 293 \u00b7 jpeg","desc":"lifecycle data security stages cloud management architecture follows subtle hides typically following","filetype":"jpg","width":484,"height":293,"domain":"agileanswer.blogspot.com","created_at":null,"updated_at":null,"id":5705,"keyword_id":698,"url":"https:\/\/cdn.xl.thumbs.canstockphoto.com\/data-security-lifecycle-pictures_csp17456388.jpg","link":"https:\/\/www.canstockphoto.com\/images-photos\/lifecycle.html","title":"Lifecycle Images and Stock Photos. 3,903 Lifecycle photography and","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.XWjM1ZtwkzhUkieBQTgKrgAAAA&pid=15.1","size":"265 x 194 \u00b7 jpeg","desc":"lifecycle vaeenma security data royalty cycle development system","filetype":"jpg","width":265,"height":194,"domain":"www.canstockphoto.com","created_at":null,"updated_at":null,"id":5706,"keyword_id":698,"url":"https:\/\/cdn.securosis.com\/assets\/library\/main\/lifecycle2.png","link":"https:\/\/securosis.com\/blog\/10046","title":"Securosis - Blog - Article","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.Qzw8MB1m3WDeIAvFNFv8lQHaFj&pid=15.1","size":"1506 x 1128 \u00b7 png","desc":"lifecycle","filetype":"png","width":1506,"height":1128,"domain":"securosis.com","created_at":null,"updated_at":null,"id":5707,"keyword_id":698,"url":"http:\/\/www.esds.co.in\/kb\/wp-content\/uploads\/2010\/12\/Cloud-Computing-Framework.jpg","link":"https:\/\/www.esds.co.in\/kb\/a-framework-for-cloud-computing\/","title":"A Framework for Cloud Computing","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.5uUfHCAr8fpHugU_vvDrKQHaFj&pid=15.1","size":"976 x 732 \u00b7 jpeg","desc":"cloud framework computing characteristics platform","filetype":"jpg","width":976,"height":732,"domain":"www.esds.co.in","created_at":null,"updated_at":null] this site you are coming to the right page. Contains many images about cloud data security lifecycle Lifecycle vaeenma security data royalty cycle development system. Don't forget to bookmark this page for future reference or share to facebook / twitter if you like this page.
No comments:
Post a Comment