If you are searching about Is My Data Safe in the Clouds?Cloud Computing and Related Security you've came to the right place. We have 9 Images about Is My Data Safe in the Clouds?Cloud Computing and Related Security like data security in cloud| trends in cloud security | Cloud Computing, Eight Risks and Challenges for Cloud Computing – Skill Monk and also Is My Data Safe in the Clouds?Cloud Computing and Related Security. Here it is:
Is My Data Safe In The Clouds?Cloud Computing And Related Security
 securereading.com
securereading.com cloud data computing security challenges threats issues technology related clouds safe key service alliance shared industry points loss
Data Security In Cloud| Trends In Cloud Security | Cloud Computing
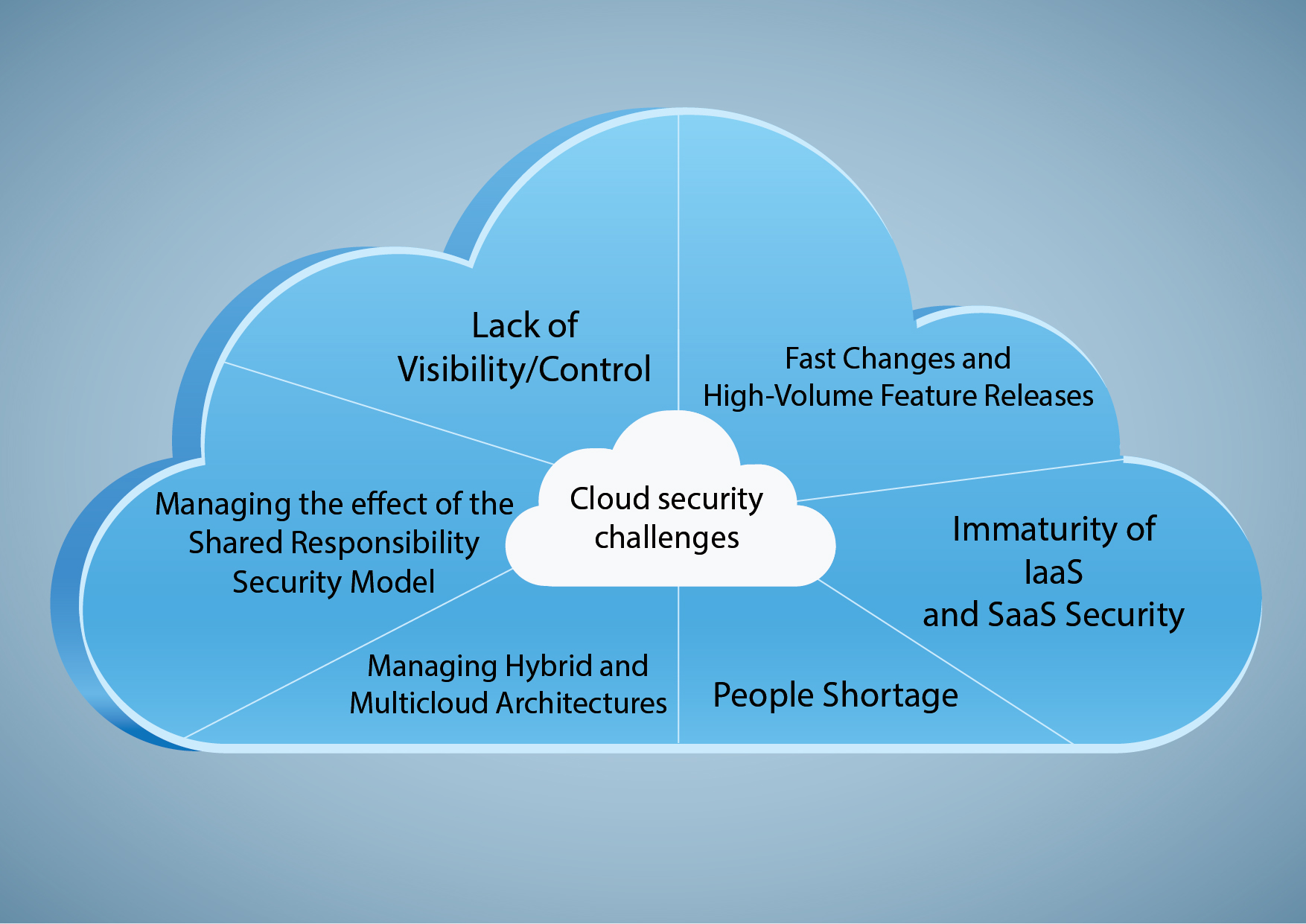 www.suntechnologies.com
www.suntechnologies.com lack computing visibility suntechnologies
4 Key Data Security Challenges In Cloud Computing - Techiexpert.com
 www.techiexpert.com
www.techiexpert.com cloud security computing data challenges key applications enterprise grade snp techiexpert secure
Latest Cloud Computing Threats To Organizations & Prevention Strategies
cloud security issues challenges computing tips data threats securing solution privacy attacks mobile prevention device lab organizations strategies latest
Data Security Challenges In Cloud Computing - ZNetLive Blog - A Guide
 www.znetlive.com
www.znetlive.com cloud data computing challenges security 2021 znetlive wire19 environment major challenge field technology been
Data Security Statistics - Understanding Cloud Data Security Risks
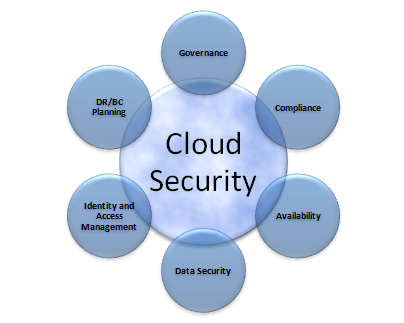 www.access-smart.com
www.access-smart.com saas
Eight Risks And Challenges For Cloud Computing – Skill Monk
 blog.skillmonks.com
blog.skillmonks.com challenges computing
Security In Cloud Computing: Guide For Beginners - Cyber Coastal
 cybercoastal.com
cybercoastal.com computing attacks telcos telco isp
Cloud Security Challenges | Download Scientific Diagram
 www.researchgate.net
www.researchgate.net Cloud security computing data challenges key applications enterprise grade snp techiexpert secure. Latest cloud computing threats to organizations & prevention strategies. Data security statistics
if you are looking "id":695,"keyword_id":33,"name":"data security challenges in cloud computing","scraped_at":"2022-12-16 03:31:23","created_at":"2022-12-16T03:31:23.000000Z","updated_at":"2022-12-16T03:31:23.000000Z","images":[ Cloud Computing","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.8QhS9gGvIk2InBT4qYh46AHaFP&pid=15.1","size":"1754 x 1241 \u00b7 jpeg","desc":"lack computing visibility suntechnologies","filetype":"jpg","width":1754,"height":1241,"domain":"www.suntechnologies.com","created_at":null,"updated_at":null,"id":6273,"keyword_id":695,"url":"https:\/\/blog.skillmonks.com\/wp-content\/uploads\/2020\/08\/Eight-Risks-and-Challenges-for-Cloud-Computing-6.jpg","link":"https:\/\/blog.skillmonks.com\/eight-risks-and-challenges-for-cloud-computing\/","title":"Eight Risks and Challenges for Cloud Computing \u2013 Skill Monk","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.BsUe0WHzH1PgXG1bvN9JJwHaHa&pid=15.1","size":"1080 x 1080 \u00b7 jpeg","desc":"challenges computing","filetype":"jpg","width":1080,"height":1080,"domain":"blog.skillmonks.com","created_at":null,"updated_at":null,"id":6274,"keyword_id":695,"url":"http:\/\/www.techpluto.com\/wp-content\/uploads\/2014\/12\/securing-cloud-data1.png","link":"https:\/\/www.techpluto.com\/latest-cloud-computing-threats-to-organizations-prevention-strategies\/","title":"Latest Cloud Computing Threats To Organizations & Prevention Strategies","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.OTlx37aYu8d80zv-bNPwNQHaEs&pid=15.1","size":"716 x 454 \u00b7 png","desc":"cloud security issues challenges computing tips data threats securing solution privacy attacks mobile prevention device lab organizations strategies latest","filetype":"png","width":716,"height":454,"domain":"www.techpluto.com","created_at":null,"updated_at":null,"id":6275,"keyword_id":695,"url":"https:\/\/securereading.com\/wp-content\/uploads\/2016\/09\/cloud-computing_1_2017.png","link":"https:\/\/securereading.com\/is-my-data-safe-in-the-clouds\/","title":"Is My Data Safe in the Clouds?Cloud Computing and Related Security","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.WKFCzGZFoBZwtl0JZTN4eAHaFj&pid=15.1","size":"975 x 731 \u00b7 png","desc":"cloud data computing security challenges threats issues technology related clouds safe key service alliance shared industry points loss","filetype":"png","width":975,"height":731,"domain":"securereading.com","created_at":null,"updated_at":null,"id":6276,"keyword_id":695,"url":"https:\/\/www.techiexpert.com\/wp-content\/uploads\/2019\/05\/Data-security-challenges-in-cloud-computing.jpg","link":"https:\/\/www.techiexpert.com\/4-key-data-security-challenges-in-cloud-computing\/","title":"4 key data security challenges in cloud computing - Techiexpert.com","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.uAFCadLpn0aD4O8ZcD9JbgHaES&pid=15.1","size":"1024 x 594 \u00b7 jpeg","desc":"cloud security computing data challenges key applications enterprise grade snp techiexpert secure","filetype":"jpg","width":1024,"height":594,"domain":"www.techiexpert.com","created_at":null,"updated_at":null,"id":6277,"keyword_id":695,"url":"https:\/\/cybercoastal.com\/wp-content\/uploads\/2021\/04\/img_0241.jpg","link":"https:\/\/cybercoastal.com\/security-in-cloud-computing-guide-for-beginners\/","title":"Security in Cloud Computing: Guide For Beginners - Cyber Coastal","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.-ARZndxGEYH4FJtBtn4jJgHaEk&pid=15.1","size":"560 x 345 \u00b7 jpeg","desc":"computing attacks telcos telco isp","filetype":"jpg","width":560,"height":345,"domain":"cybercoastal.com","created_at":null,"updated_at":null,"id":6278,"keyword_id":695,"url":"https:\/\/www.access-smart.com\/wp-content\/uploads\/2011\/12\/cloudsecurity.png","link":"http:\/\/www.access-smart.com\/data-security\/cloud\/","title":"Data Security Statistics - Understanding cloud data security risks","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.0WUjjUKDylyvpTqiNi7y0wAAAA&pid=15.1","size":"404 x 323 \u00b7 png","desc":"saas","filetype":"png","width":404,"height":323,"domain":"www.access-smart.com","created_at":null,"updated_at":null, Download Scientific Diagram","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.zjGHY5-GrmNM5Zw9DRGKUAHaEO&pid=15.1","size":"850 x 485 \u00b7 png","desc":"","filetype":"png","width":850,"height":485,"domain":"www.researchgate.net","created_at":null,"updated_at":null,"id":6280,"keyword_id":695,"url":"https:\/\/www.znetlive.com\/blog\/wp-content\/uploads\/2020\/10\/cloud-computing-featured-compressed.jpg","link":"https:\/\/www.znetlive.com\/blog\/data-security-challenges-in-cloud-computing\/","title":"Data security challenges in cloud computing - ZNetLive Blog - A Guide","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.b0XQi73JvB0bLLqGxzxauQHaEo&pid=15.1","size":"1000 x 625 \u00b7 jpeg","desc":"cloud data computing challenges security 2021 znetlive wire19 environment major challenge field technology been","filetype":"jpg","width":1000,"height":625,"domain":"www.znetlive.com","created_at":null,"updated_at":null] this site you are coming to the right page. Contains many images about data security challenges in cloud computing Is my data safe in the clouds?cloud computing and related security. Don't forget to bookmark this page for future reference or share to facebook / twitter if you like this page.
No comments:
Post a Comment